Smartphones have become an integral part of daily life, but this convenience comes with significant privacy risks. Recent research highlights how sophisticated spyware applications can covertly monitor users, leaking sensitive personal data without their knowledge. Understanding how these apps operate, their vulnerabilities, and the steps you can take to safeguard your device is crucial in today’s digital landscape.
While these malicious applications are often marketed as tools for parental supervision or employee oversight, they are frequently exploited by malicious actors to secretly monitor spouses or partners. Such spyware apps require minimal technical skills to install, offering straightforward instructions and only needing temporary access to the target device. Once installed, they run discreetly in the background, capturing everything from text messages and emails to photos and voice calls. This data is then accessible to the abuser through a web portal, making privacy breaches alarmingly easy to carry out.
Studies from cybersecurity firms reveal a sharp rise in spyware infections. Norton Labs reported a 63% increase in the number of devices infected in the U.S. between September 2020 and May 2021, while Avast observed a 93% surge in the UK over a similar period. These figures underscore the growing threat and the importance of vigilance. To check if your device has been compromised, it’s recommended to review your privacy settings and app list in your device’s configuration, as spyware often hides within legitimate-looking apps or disguises itself as system components.
Enze Liu, a lead author of a recent paper titled No Privacy Among Spies: Assessing the Functionality and Insecurity of Consumer Android Spyware Apps, emphasizes raising awareness about these issues. Liu, a Ph.D. student at UC San Diego, notes that this problem affects not only individuals but also the broader research community. Their team plans to present findings on spyware vulnerabilities at the upcoming Privacy Enhancing Technologies Symposium in Zurich, Switzerland.
The team conducted a comprehensive analysis of 14 prominent spyware applications designed for Android devices. Unlike iPhones, which restrict app installation outside official stores, Android devices allow these invasive apps to be downloaded from the web, increasing their prevalence. These apps can operate in the background without visible icons, often masquerading as innocuous system symbols such as Wi-Fi or internet icons, making detection challenging. For example, one such app, Spyhuman, disguises itself as a simple WiFi icon on an Android launcher, concealing its true nature.
What Are Spyware Applications?
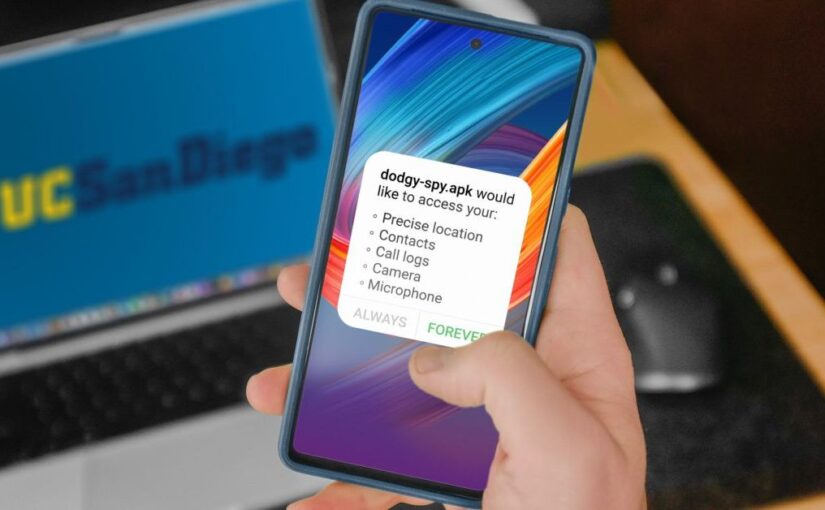
Spyware apps are malicious programs that secretly run on a device, often without the user’s awareness. Their primary purpose is to gather sensitive data, including location information, text messages, call logs, audio recordings, and even live video streams. All the collected information is transmitted to an online control panel, allowing the abuser to monitor the victim remotely.
These apps are relatively affordable, typically costing between $30 and $100 per month, making them accessible to a broad audience. They are designed for easy installation on smartphones, requiring no advanced technical skills. However, they do need temporary physical access to the target device to be installed and configured, as they are not available through legitimate app stores.
To learn more about how to record gameplay for streaming or sharing purposes, you might explore resources on methods to record Steam gameplay on Windows and Mac, which can be useful for gamers and content creators alike.
How Do Spyware Apps Collect Data?
Spyware applications employ a variety of techniques to covertly capture user information. One method involves using an invisible browser that streams live video from the device’s camera to a remote server. Others activate the microphone to record calls or ambient sounds, sometimes even turning on the device’s speaker to eavesdrop on conversations.
Many apps exploit accessibility features intended for visually impaired users. These features can be manipulated to record keystrokes or read on-screen information, providing a backdoor for data collection. Additionally, spyware often hides itself by not appearing in the app launcher or by masquerading as common system icons like Wi-Fi or internet indicators.
Some spyware apps can accept commands via SMS messages. Alarmingly, certain applications execute commands regardless of whether the message is from an authorized user, including commands to remotely wipe the device or access stored data.
Data Security Weaknesses in Spyware
The security of data collected by these applications is often weak or nonexistent. Many spyware apps transmit data through unencrypted channels, exposing sensitive information such as photos, location data, and login credentials to potential interception over WiFi networks. Only a few of the studied apps employ encryption, leaving user data vulnerable to hacking.
Furthermore, many apps store collected data in publicly accessible URLs or predictable locations, allowing anyone with the link to retrieve this information. Some even retain data after the user has deleted the app or canceled their subscription, risking prolonged exposure of private details. For example, one app kept all user data accessible on its servers, even after the user’s account was terminated or the license expired.
To mitigate these risks, users should routinely review their device’s app permissions and privacy dashboard. For more detailed guidance, refer to resources on detecting installed games on Steam or repair procedures for Steam games.
How to Protect Against Spyware
Preventing spyware infections requires proactive measures. The researchers recommend that Android manufacturers enforce stricter controls on app icon visibility, ensuring that all installed apps are visible in the launcher. Many spyware apps resist uninstallation by automatically restarting or re-installing after removal; thus, monitoring tools and dashboards that alert users to suspicious activity are essential.
Android’s native indicators for microphone and camera use can help, but they are not foolproof, especially when legitimate apps trigger these indicators. The researchers advocate for enhanced privacy dashboards that log all access to sensitive data, along with periodic notifications informing users of apps with excessive permissions.
Additional steps include installing reputable security apps, avoiding sideloading unknown apps, and regularly reviewing app permissions and activity logs. For a comprehensive approach to managing Android device security, consult mastering Android game file editing: a complete guide, which offers insights into safeguarding your device’s integrity.
Disclosures, Safeguards, and Future Directions
The research team disclosed their findings to the affected app developers, but no responses had been received by publication. To prevent misuse, the team will only share their tools with verified users who demonstrate legitimate intent.
Future research will expand on the supply chain of spyware development, particularly focusing on apps originating from China and Brazil. Addressing this widespread problem requires a multifaceted approach involving industry, government, and law enforcement. Measures such as financial transaction restrictions by companies like Visa and PayPal, regular crackdowns, and stricter legal enforcement are necessary to curb this growing threat.
The study was supported by the National Science Foundation and the UC San Diego Center for Networked Systems, emphasizing the importance of ongoing work in this area to protect digital privacy.
For more details on securing your mobile device and understanding the risks, visit completing Android game file modifications.
—
Protect your privacy by staying informed and vigilant against hidden threats lurking on your smartphone.